Gibson's ENcryption-Enhanced Spoofing Immunity System
| Edited: Jan 12,2001 at 16:23 (-0700 UTC) | . . . because sometimes it IS rocket science! |
|
Eliminate Denial of Service (DoS) Vulnerability Part II - Exploring the Solution by Steve Gibson
The GENESIS System |
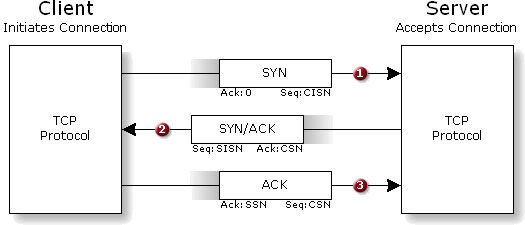
Connection Management Deferral: The first innovation applied to the TCP protocol is the deferral of all "connection management" until the end of the standard 3-way TCP handshake. In other words, rather than storing connection information upon the receipt of the Client's first SYN packet (as the traditional TCP protocol suggests) we instead refuse to take the connection "seriously" until we have received the Client's ACK packet. Let's refer to our 3-way TCP connection handshake diagram to see how this can be accomplished:
As shown in the familiar diagram above, the third and final handshake packet is the ACK packet sent from the Client to the Server. The key to deferring all connection establishment work until the receipt of this packet is noticing that this ACK packet contains every piece of information required to define the connection. It contains both the Client's current Sequence Number (CSN) and the Server's Sequence Number (SSN), which this packet is acknowledging. And since each TCP/IP packet contains the packet's source and destination IP addresses and the source and destination TCP port numbers . . .
for the current state of the connection. This means that we do not need to save ANY information about the pending connection after receiving the Client's initial SYN packet. When a SYN packet is received, we respond with a valid SYN/ACK packet, ACKnowledging the receipt of the Client's SYN and providing our own initial sequence number (ISN) . . . then we forget all about the pending connection! If the Source IP of the SYN packet was spoofed, our replying SYN/ACK will fly off into Internet oblivion, but we will not be in any way damaged by the connection that never follows because we will have already forgotten about it. Only if the Client replies to the receipt of our SYN/ACK with an ACK packet, do we finally need to get serious about the connection. At that time we would allocate the resources to manage it further, recording the complete connection information obtained from the ACK packet. This is an entirely workable solution as it is, and we are completely immune to SYN flooding. But we do have one big problem . . .
Whoops. We quickly see that the only thing we've achieved so far is pushing the same problem we had before back further in the handshake process. Now, a malicious hacker can flood us with spoofed ACK packets to cause us to establish falsified connections and quickly overwhelm our Server's resources. But we HAVE achieved something
important:
ACK packets which are valid replies to our SYN/ACK, and those that we can discard as spoofing attempts. Encrypted Tokens: |
Authenticating the Client The second innovation applied to the TCP protocol is the explicit, non-spoofable, cryptographic authentication of the remote Client's IP address. Authentication of the Client's IP, prior to the committment of any connection resources, provides all of the benefits of Connection Management Deferral with none of the liabilities.
The cryptographic community understands, more than any other group, that very little security is achieved through obscurity. Applying that to our context: Relying upon the hope that a malicious hacker will not have discovered something about the operation of a system, and depending upon this obscurity for the system's "security", is a really bad idea. Consequently, a paramount requirement for this new hacker-proof TCP technology is that it can withstand the full disclosure of every aspect of its operation without sacrificing any of its security. This has been achieved. Another concept from the security community is that the simplest solutions, lacking convoluted exceptions and complex bells and whistles, are the most provably secure. The solution I developed and present here is surprisingly simple and straightforward:
BINGO!! It is just that simple! The use of strong encryption creates an unknowable and non-discoverable relationship between the more than FOUR BILLION (32-bits) possible Internet addresses and the corresponding more than FOUR BILLION (32-bits) matching Encrypted Tokens. The only way for a remote Client to receive an encrypted token that correctly matches any address on the Internet is for it to send a SYN packet to the Server providing that address. Since it must also receive the Server's SYN/ACK reply containing the matching token, the Source IP address provided by the Client must be authentic (or the Server's reply won't return to the Client). When a properly matching encrypted token is returned with the Client's ACK packet, we know that the Client could have only received the encrypted token from us and that the token must have made a successful round trip to the Client and back. Thus, the Client's IP address, and its desire for a TCP connection with the Server, is perfectly authenticated and the Server may confidently establish a TCP connection. Repeating and
Summarizing
Cool, huh?? |
What About This Encryption? Ronald Rivest, working in conjunction with RSA Laboratories, has invented a number of highly regarded cryptographic ciphers, systems and technologies. For our purposes, we require a cipher which is very fast since every received SYN packet requires an encryption of the apparent Source IP to generate the matching encrypted token, and every received ACK packet (describing a non-established connection) requires a decryption of the returned encrypted token to verify its IP match.
well known and extremely strong RSA RC5 cipher. RC5 is a high-performance, parameterized, symmetric cipher. One of the most interesting characteristics of RC5 is that its "cipher strength" can be directly controlled through its parameters. The most important of these is the number of "rounds", or iterations, the algorithm uses. This essentially feeds the results of one "pass" back into the cipher for another. RSA recommends at least 12 rounds for good security but it's so fast I'm using many more. How secure is RC5? To all that, add the following:
Encrypting the Client's IP address with a fast symmetric cipher, like RC5, provides an uncrackable and completely "opaque" token for use in authenticating the token's round-trip and therefore the IP address of the remote Client. Since the token is directly generated from the Client's IP address, the SYN-triggered generation and ACK-triggered verification are able to operate independently, tied together only by the Client's IP address. RSA's next-generation cipher, RC6, is even stronger than RC5 (not that we need any more strength) and, if adopted as the next international encryption standard to replace the rapidly weakening DES, RSA has promised to make the use of RC6 completely free. (I already own a licence to use RC5.)
|
Initial Sequence Number Details The third and final innovation satisfies a "safety requirement" of the TCP protocol which our use of an initial sequence number that's simply based upon the Client's IP address was failing to meet. To understand the safety requirement, and our solution, we first need to learn . . . The whole truth about sequence
numbers Now, you might wonder why TCP bothers with all of this "Initial Sequence Number" stuff at all? For example, why not simply start numbering a connection's data stream at ZERO or ONE, and just count up from there? The reason involves the need for the "reusability" of any given connection: TCP allows connections to be closed and immediately re-opened and reused. But, if an existing connection were quickly closed and immediately re-opened, and if the new connection's initial sequence number was the same as the first, then data packets arriving late from the previous connection could be confused with packets from the new connection because their sequence numbers would be so similar. But, if the new connection were to use an initial sequence number much larger than the previous connection's, then any late arrivals from the previous connection would have sequence numbers lower than the initial sequence number of the new connection, and could be immediately discarded. The TCP protocol specifies that each machine should maintain a 32-bit counter which is increased by one approximately every 4 microseconds. This current count is then used to supply the Initial Sequence Number anytime TCP is establishing a new connection. In this way we are assured that quickly reused connections will have very distinct sequence numbers so that old packets can be easily identified as such. But now we see the problem with my scheme for basing our own Initial Sequence Numbers upon the Client's encrypted IP address. Since a quickly reused connection would have the same IP address as the last connection, we would use the same ISN for the new connection and create exactly the problem that Initial Sequence Numbers were designed to prevent!
But fear not . . . I've solved that problem
too!
to the ISN we generate from the Client's IP address! Here's how it works:
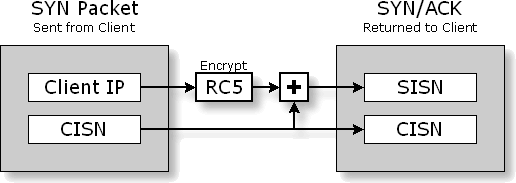
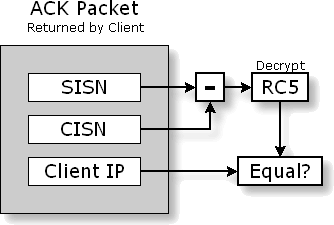 It's beautiful and perfect. What we are doing, conceptually, is using the Client's 32-bit Initial Sequence Number counter as our own. We can't use our own, since we need to hold the Client's encrypted IP there. So we add the Client's ISN to our encryption result in order to create the required "per-connection" changing ISN used to uniquely number our future packets. Since both packets from the Client (its initial SYN and its ACK) contain its ISN, we are able to use that as a "fixed bias" to our encryption — adding it before we send the SYN/ACK and subtracting it when we receive the ACK. Since the Client's ISN, complying with the TCP protocol, will be changed and much larger for a second connection, the ISN we supply to the Client will too, since we're simply adding it's own ISN to our fixed encryption result to form our ISN! Is that cool or what?!! Does this have any impact on our
authentication security? Thus, we are every bit as secure as we were, while also being fully compliant with the "increasing Initial Sequence Number" requirement of the TCP protocol! |
Deploying GENESIS So, what does this all mean? It means that . . .
This system may be transparently incorporated into any and all TCP protocol implementations. Doing so would render the GENESIS-using devices and machines completely immune to the consequences of SYN and ACK address spoofing Denial of Service attacks. Mainstream operating systems Personal firewalls and
routers Previous DoS solutions
robust solution to the problem of TCP Denial of Service attacks. (of the SYN & ACK spoofed IP flooding varieties) For a detailed analysis of previous solutions, Part III - Acknowledgement of Previous
Work |
 |
 |
 |
 |
 | ||||
| Purchasing Info | GRC Mail System | To GRC's Home | Tech Support | Discussions |
The contents of this page are Copyright (c) 2000 by Gibson Research Corporation.
SpinRite, ChromaZone, ShieldsUP, NanoProbe, the character 'Moe' (shown above),
and the slogan "It's MY Computer" are registered trademarks of Gibson Research
Corporation (GRC), Laguna Hills, CA, USA. GRC's web and customer privacy policy.
~ ~ ~